Spot the bug!
Test your skills in spotting the security bugs in code snippets!
Test 1
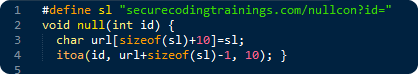
Click here for the solution
The URL is created to the "url" variable from two parts. First, the fixed part is copied to the local "url" variable and then the URL is appended with the string representation of the "id" function parameter. Although the MAX_INT (2147483647, 10 character long) will fit into the local buffer, the MIN_INT (-2147483648) won't, because its string representation is one character larger than the MAX_INT. In the example, if the attacker calls the function with value from the range -1000000000 - -2147483648, the itoa function call will cause a stack overflow.
Test 2

Click here for the solution
Depending on the used compiler (tested with Visual Studio 2008), the vulnerable "s" function will leak the secret password (stored in the pwd buffer) if the received "u" parameter contains at least 12 characters long string. It is because; the strncpy function does not insert a closing 0 at the end of the string if it reaches the maximum number of copied bytes. So, the printf will show both the "n" and "pwd" buffers.
Additionally it also contains format string vulnerability also, because the received "u" parameter is passed to the printf function without specifying a format string. So, the attacker can insert format specifiers into the input string, which will be handled by the printf and could cause information leakage or even arbitrary code execution.
Test 3
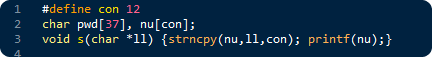
Click here for the solution
Depending on the used compiler (tested with Visual Studio 2008), the vulnerable "s" function will leak the secret password (stored in the pwd buffer) if the received "ll" parameter contains at least 12 characters long string. It is because; the strncpy function does not insert a closing 0 at the end of the string if it reaches the maximum number of copied bytes. So, the printf will show both the "nu" and "pwd" buffers.
Additionally it also contains format string vulnerability also, because the received "ll" parameter is passed to the printf function without specifying a format string. So, the attacker can insert format specifiers into the input string, which will be handled by the printf and could cause information leakage or even arbitrary code execution.
Test 4

Click here for the solution
Although the function checked whether the received string and buffer will fit into the local variable before the memcpy, if the attacker call this function with a very large number (e.g. 0xffffffff), an arithmetic integer overflow will occur and the strlen(n)+ll will smaller than the size of the local buffer, but the memcpy will copy a large amount of data to the local buffer and will cause a stack buffer overflow.
Test 5

Click here for the solution
Although the function checked whether the received string and buffer will fit into the local variable before the memcpy, if the attacker call this function with a very large number (e.g. 0xffffffff), an arithmetic integer overflow will occur and the strlen(s)+ab will smaller than the size of the local buffer, but the memcpy will copy a large amount of data to the local buffer and will cause a stack buffer overflow.



